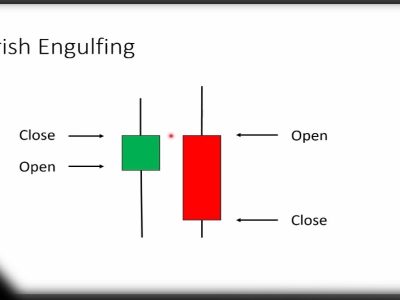
Crypto gateway is a software or hardware-software complex operating on the basis of VPN (Virtual Private Network) technology and providing “transparent” encryption of information network flows between objects that are distant from each other.
The use of crypto high-risk gateway is necessary if it is necessary to ensure the integrity and confidentiality of transmitted data that is sent over unsecured or unverified communication channels. VPN in this case can be organized on the principle of “network-network” or “network-remote user”. If the network-to-network principle is used, then the cryptographic gateway must be installed on both sides of the communication channel. In this case, the traffic between them will be encrypted. In the case of using the “network-remote user” principle, a software or hardware crypto-gateway is installed on the server side, the user only needs to install the software client.
Access to secure network resources
The access server (crypto-gateway software) identifies and authenticates users and connects them to the necessary network nodes. The created secure channels form VPN networks. To ensure the operation of such a network, specialized software (control center) is used, which manages local security policies for clients and sends configuration data to all users, keeps system logs.
Functionality
The basic functions of crypto gateways are as follows:
- protecting the confidentiality and integrity of transmitted IP packets;
- authentication of remote hosts and users;
- hiding the topology of the internal network by encapsulating traffic in an encrypted data channel.
Nowadays blockchain payment system often act as firewalls. But not in every case they can be as flexible and customizable, that is, they cannot be compared with their functionality with a full-fledged firewall.
Differences and features of cryptographic gateways
Nowadays, many technological and circuit solutions have been developed for organizing secure data transmission over a network. The most common technology is the Hub-and-Spoke class cryptographic protection, in which each communication channel is connected to the center, and Full Mesh, in which all channels are interconnected. Individual developers can implement VPN technologies in their own way.
From the point of view of the protocols used, crypto-gateways with Virtual Private Network can be divided into:
- proprietary protocols (private developments) that are incompatible with any other solutions;
- IPSec/IKE class protocols (IP Security and The Internet Key Exchange);
- SSL/TLS class protocols (sockets layer and transport layer security).
Cryptographic gateways can be used in the following cases:
- To protect personal data in the network of a particular enterprise.
- To protect confidential information in accordance with applicable law. For example, while maintaining access to professional or commercial secrets, data on insured people, etc.
- To protect data stored in the networks of executive authorities.
- To prevent unauthorized interception of any information (for example, about commercial orders of various organizations, as well as the services they provide, if we are talking about government activities).
- To protect data owned by any government agencies or enterprises working with government orders.