If you are new to the world of computer science, you may have heard the term “hashing” come up in discussions about data security and encryption. In this beginner’s guide, we will explore what hashing is, why it is important, the different types of hashing algorithms, how they work, and the security implications of using them.
You can also read: Wyckoff Analysis Demystified
What is Hashing?
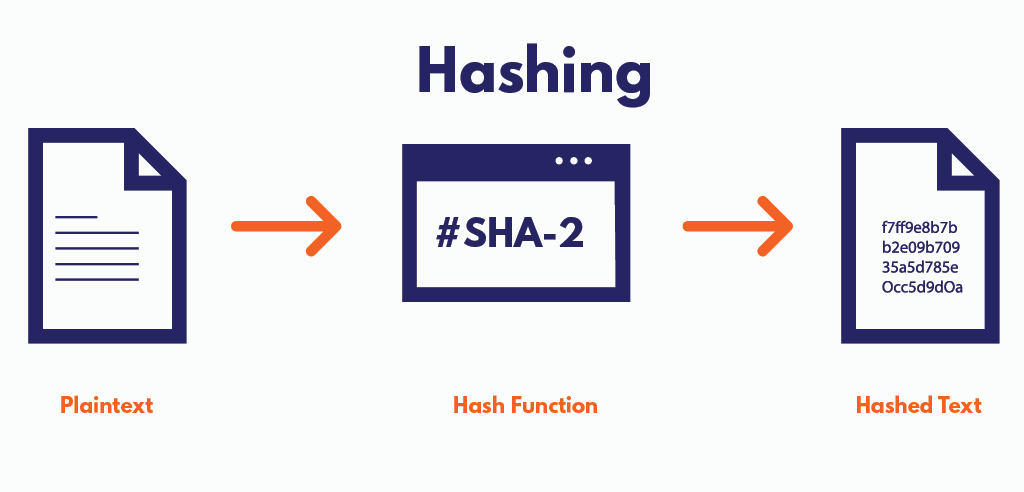
Hashing is a fundamental concept in computer science that involves taking input data of any size and producing a fixed-size output, which is called a hash. The input data can be anything, such as a password, a file, or a message. The hash function used to create the hash value is a mathematical algorithm that performs a series of operations on the input data to create the output hash value.
The hash value is a unique representation of the input data, meaning that even a small change in the input data will result in a completely different hash value. This unique property of hashing makes it useful for a wide range of applications, including data integrity, password storage, and digital signatures.
One of the primary uses of hashing is data integrity. When data is transmitted or stored, there is always a risk of it being modified or tampered with. Hashing can be used to ensure that the data has not been changed by creating a hash value of the original data before it was transmitted or stored, and then comparing it to a hash value of the received or retrieved data. If the two hash values match, it means that the data has not been modified.
Another important application of hashing is password storage. Instead of storing passwords in plain text, which can be easily accessed by attackers if the database is breached, the password can be hashed and the hash value can be stored in the database. When a user enters their password to log in, the password is hashed again and compared to the stored hash value to verify that the password is correct. This technique is called password hashing and is
Hashing is also used in digital signatures, which are used to verify the authenticity and integrity of digital documents. In a digital signature, a hash value of the document is created, and then the hash value is encrypted using the sender’s private key. The encrypted hash value is then attached to the document and sent to the receiver. The receiver can then use the sender’s public key to decrypt the hash value and compare it to a hash value that they create themselves from the received document. If the two hash values match, it means that the document has not been modified and that it was sent by the sender.
Why is Hashing Important?
Hashing is important for several reasons, including data integrity, password security, and digital signatures.
Data integrity is a critical aspect of information security. When data is transmitted or stored, there is always a risk of it being modified or tampered with. Hashing can be used to ensure that the data has not been changed by creating a hash value of the original data before it was transmitted or stored and then comparing it to a hash value of the received or retrieved data. If the two hash values match, it means that the data has not been modified. This technique is widely used in secure systems to ensure that data remains accurate and trusted.
Password security is another important application of hashing. When a user creates a password for an online account, the password is hashed and stored in the website’s database. When the user enters their password to log in, the password is hashed again, and the hash value is compared to the stored hash value to verify that the password is correct. This technique is called password hashing, and it is used to store passwords securely. By storing the hash value instead of the plaintext password, even if an attacker gains access to the database, they will not be able to retrieve the original password.
Digital signatures are used to verify the authenticity and integrity of digital documents. In a digital signature, a hash value of the document is created, and then the hash value is encrypted using the sender’s private key. The encrypted hash value is then attached to the document and sent to the receiver. The receiver can then use the sender’s public key to decrypt the hash value and compare it to a hash value that they create themselves from the received document. If the two hash values match, it means that the document has not been modified and that it was sent by the sender. This technique ensures that the document is authentic and has not been modified during transmission.
Hashing is also used in other applications, such as digital forensics, file verification, and data deduplication. In digital forensics, hashing can be used to create a unique identifier for digital evidence, which can be used to track and analyze the evidence. In file verification, hashing can be used to ensure that the downloaded file is the same as the original file by comparing the hash value of the downloaded file to the hash value of the original file. In data deduplication, hashing can be used to identify and remove duplicate data, which can save storage space and improve system performance.
Types of Hashing Algorithms
There are several types of hashing algorithms, each with its own strengths and weaknesses. Some of the most commonly used hashing algorithms include:
- MD5 (Message Digest 5): MD5 is an older hashing algorithm that produces a 128-bit hash value. It is fast and easy to compute, but it is no longer considered secure because it is vulnerable to collision attacks, where two different inputs produce the same hash value.
- SHA-1 (Secure Hash Algorithm 1): SHA-1 is another older hashing algorithm that produces a 160-bit hash value. Like MD5, it is fast and easy to compute, but it is also vulnerable to collision attacks and is no longer considered secure.
- SHA-256 (Secure Hash Algorithm 256): SHA-256 is a newer hashing algorithm that produces a 256-bit hash value. It is slower than MD5 and SHA-1 but is considered to be more secure and is widely used in modern applications.
- SHA-512 (Secure Hash Algorithm 512): SHA-512 is a newer hashing algorithm that produces a 512-bit hash value. It is slower than SHA-256 but is considered to be even more secure and is used in applications that require high levels of security, such as financial transactions.
- RIPEMD-160 (RACE Integrity Primitives Evaluation Message Digest): RIPEMD-160 is a hashing algorithm that produces a 160-bit hash value. It is similar to SHA-1 but is considered to be more secure and is commonly used in digital signature applications.
- Blake2: Blake2 is a newer hashing algorithm that produces hash values of various sizes, including 256-bit and 512-bit hash values. It is faster than SHA-256 and SHA-512 and is used in applications that require high-speed hashing, such as password hashing and data deduplication.
- Scrypt: Scrypt is a hashing algorithm that is designed to be computationally expensive, making it more difficult for attackers to guess the input data. It is commonly used in password-hashing applications and is considered to be more secure than other hashing algorithms.
How Does a Hashing Algorithm Work?
A hashing algorithm works by taking in data of any size and applying a series of mathematical operations to produce a fixed-size hash value. The hash value is a unique representation of the input data, meaning that even a small change in the input data will result in a completely different hash value.
The process of hashing begins by taking the input data and breaking it down into a fixed-size block. The hashing algorithm then applies a series of mathematical operations to the block to produce a hash value. The hash value is then combined with the next block of data, and the process is repeated until all the input data has been processed.
The mathematical operations used in hashing algorithms are designed to be fast and easy to compute but must also be secure and difficult to reverse. One common operation used in hashing algorithms is the bitwise XOR operation, which compares two bits and returns a 1 if they are different and a 0 if they are the same. Other common operations include rotating bits, shifting bits, and modular arithmetic.
In addition to the mathematical operations, hashing algorithms may also use a salt value to further increase the security of the hash value. A salt value is a random value that is added to the input data before it is hashed, making it more difficult for attackers to guess the input data.
Once the hash value has been produced, it can be used for a variety of purposes, including data integrity, password storage, and digital signatures. The hash value can be compared to a previously generated hash value to verify that the data has not been modified, or it can be used to store a password securely by storing the hash value instead of the plaintext password.
It is important to note that while hashing algorithms are designed to be secure and difficult to reverse, they are not foolproof. Attackers can use brute force methods to guess the original input data by trying different combinations of input data until they produce the same hash value. Additionally, if two different inputs produce the same hash value, it is called a collision, and this can be exploited by attackers to bypass security measures.
Pros and Cons of Different Hash Algorithms
Hash algorithms are widely used in data security and integrity verification applications. Here are some common hash algorithms with their pros and cons:
1. MD5 (Message Digest 5)
Pros:
– Fast computation speed
– Widely used and supported by many applications
Cons:
– Vulnerable to collision attacks, meaning that it is possible to generate two different messages with the same hash value
– Not recommended for use in new applications due to its security weaknesses
2. SHA-1 (Secure Hash Algorithm 1)
Pros:
– Widely used and supported by many applications
– Faster computation speed than some other secure hash algorithms
Cons:
– Vulnerable to collision attacks
– Not recommended for use in new applications due to its security weaknesses
3. SHA-2 (Secure Hash Algorithm 2)
Pros:
– More secure than MD5 and SHA-1
– Resistant to collision attacks
Cons:
– Slower computation speed than MD5 and SHA-1
– Not as widely supported as MD5 and SHA-1
4. SHA-3 (Secure Hash Algorithm 3)
Pros:
– Resistant to collision attacks
– High-security level
– Designed to be more secure than SHA-2 and other previous hash algorithms
Cons:
– Slower computation speed than SHA-2
5. BLAKE2
Pros:
– Fast computation speed
– Resistant to collision attacks
– More secure and faster than SHA-2
Cons:
– Not as widely supported as some other hash algorithms
6. RIPEMD (RACE Integrity Primitives Evaluation Message Digest)
Pros:
– Resistant to collision attacks
– Available in different bit lengths for increased security
Cons:
– Slower computation speed than some other hash algorithms
– Not as widely supported as some other hash algorithms
The choice of hash algorithm depends on the specific application requirements, security needs, and performance considerations. While some algorithms offer faster computation speeds, others provide higher levels of security and resistance to attacks. It’s important to choose a hash algorithm that meets the specific needs of the application and to regularly evaluate its effectiveness against potential attacks.
Examples of How Hashing is Used
Hashing is used in a variety of applications, including password storage, digital signatures, and file verification. When you create a password for an online account, the password is hashed and stored in the website’s database. When you enter your password to log in, your password is hashed again and compared to the stored hash value to verify that the password is correct.
Security Implications of Hashing
Hashing is an important technique used in data security and integrity verification applications. However, there are some security implications to consider when using hashing:
1. Collision attacks: Hash algorithms can be vulnerable to collision attacks, which occur when two different messages produce the same hash value. This can be exploited by attackers to create a malicious message that has the same hash value as a legitimate message, allowing them to impersonate the legitimate message.
2. Pre-image attacks: Hash algorithms can be vulnerable to pre-image attacks, which occur when an attacker can find a message that produces a specific hash value. This can be exploited by attackers to create a message that matches a specific hash value, allowing them to bypass security measures that rely on hash values.
3. Rainbow table attacks: Rainbow table attacks are a type of pre-computed attack that can be used to crack password hashes. Attackers can pre-compute a table of possible hash values for common passwords, and then use this table to quickly find the original passwords for any hashes they encounter.
4. Hash length extension attacks: Hash length extension attacks occur when an attacker can append additional data to a hash value without knowing the original data. This can be exploited to create malicious messages that have the same hash value as legitimate messages, allowing attackers to bypass security measures that rely on hash values.
5. Side-channel attacks: Side-channel attacks are a type of attack that exploit weaknesses in the implementation of a hash algorithm rather than weaknesses in the algorithm itself. For example, an attacker could use timing or power analysis to gain information about the internal workings of the hash algorithm and use this information to deduce the original message.
To mitigate the security implications of hashing, it is important to choose a secure hash algorithm that is resistant to attacks such as collision and pre-image attacks, and use it correctly. This includes ensuring that the input message is properly randomized before hashing, and using a salt when hashing passwords to prevent rainbow table attacks. It is also important to use appropriate key management practices and to regularly evaluate the effectiveness of the chosen hash algorithm against potential attacks.
In Conclusion
In conclusion, hashing is an essential tool for data security and integrity. It allows us to ensure that data has not been tampered with and helps us store passwords securely. However, it is important to choose the right hashing algorithm for your application and to be aware of the security implications of using hashing. By understanding hashing, we can better protect our data and ensure its integrity.