As technology continues to advance, the need for security measures to protect sensitive information has become more critical than ever before. One of the most significant threats to data security is a replay attack. A replay attack is a type of cyberattack that can be costly to businesses, governments, and individuals.
In this article, we will discuss what a replay attack is, how it works, the potential consequences of a successful replay attack, and the steps you can take to prevent them.
You can also read about The Essential Guide to the EMA: Understanding Moving Averages in Trading Strategies
Introduction to Replay Attacks
A replay attack is a type of cyberattack that involves the interception and retransmission of data between two parties. The attacker intercepts data packets and then retransmits them to the original recipient. The attacker does not modify the data in any way; they merely replay it.
Replay attacks are often used to gain unauthorized access to a system or to obtain sensitive information, such as passwords or financial data.
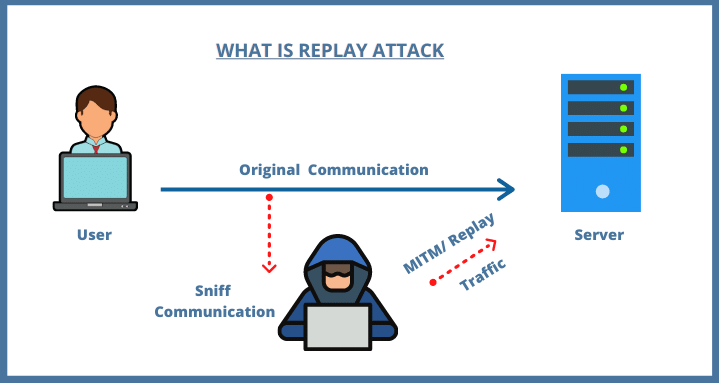
How do Replay Attacks Work?
Replay attacks work by exploiting the lack of authentication and integrity checks in a communication protocol. When data is transmitted between two parties, it is typically encrypted to ensure its confidentiality. However, encryption alone is not enough to protect against replay attacks.
In a typical replay attack, an attacker intercepts the encrypted data packets as they are transmitted between two parties. The attacker then stores these packets and retransmits them to the original recipient at a later time. The recipient is unaware that the data packets have been replayed, and they assume that they are receiving fresh data.
Replay attacks can be prevented by using various security measures, such as timestamping and nonce values.
Types of Replay Attacks
Replay attacks can occur in various contexts, including financial transactions, network communications, and authentication protocols. Here are a few examples of replay attacks in action:
1. Authentication Protocol Replay Attack
In an authentication protocol replay attack, an attacker intercepts the authentication request sent from a user to a server. The attacker then replays the authentication request multiple times, attempting to gain access to the user’s account. If successful, the attacker can access the user’s sensitive information or perform unauthorized actions on their behalf.
2. Financial Transaction Replay Attack
In a financial transaction replay attack, an attacker intercepts a legitimate transaction request between a customer and a merchant. The attacker then replays the transaction request multiple times, causing the customer to be charged multiple times for the same transaction. This can result in significant financial losses for the customer.
3. Network Communication Replay Attack
In a network communication replay attack, an attacker intercepts data packets transmitted between two parties. The attacker then replays these packets at a later time, causing the recipient to receive the same data multiple times. This can cause significant disruptions to the communication network and may result in data loss or corruption.
Consequences of a Successful Replay Attack
The consequences of a successful replay attack can be severe, depending on the context in which the attack occurs. Here are a few potential consequences of a successful replay attack:
1. Financial Losses
In a financial transaction replay attack, the victim can suffer significant financial losses. They may be charged multiple times for the same transaction or have their account drained of funds.
2. Data Loss or Corruption
In a network communication replay attack, the victim may experience data loss or corruption. This can result in the loss of critical data or the corruption of sensitive information.
3. Unauthorized Access
In an authentication protocol replay attack, the attacker may gain unauthorized access to the victim’s account. This can result in the theft of sensitive information or the unauthorized performance of actions on the victim’s behalf.
What to Do if You Are a Victim of a Replay Attack?
There are a few things you may take to lessen the harm if you find yourself the target of a repeat attack. Change any potentially compromised passwords first. Second, get in touch with your financial institution(s) and let them know there’s a chance your account may have been compromised. Keep a watchful eye on any odd behaviour on your credit record.
Replay assaults can be devastating, but you can limit the harm by acting swiftly and decisively. If you think you might be the victim of a repeat attack, be on the lookout and ready to take action.
Ways to Prevent or Limit Replay Attacks
Preventing replay attacks involves implementing various security measures to ensure the integrity and authenticity of transmitted data. Here are a few steps you can take to prevent replay attacks:
1. Timestamping
Timestamping involves adding a unique timestamp to each data packet transmitted between two parties. The timestamp ensures that each packet is unique and cannot be replayed. Timestamping is an effective way to prevent replay attacks in communication protocols.
2. Nonce Values
Nonce values are random numbers generated by a system to ensure that each data packet is unique. Nonce values are used in conjunction with timestamping to prevent replay attacks. Nonce values are often used in authentication protocols to ensure the integrity of transmitted data.
3. Encryption
Encryption is another effective way to prevent replay attacks. By encrypting data packets, an attacker cannot intercept and replay the data. Encryption ensures the confidentiality and integrity of transmitted data.
4. Message Authentication Codes (MACs)
Message authentication codes (MACs) are cryptographic algorithms used to ensure the integrity and authenticity of transmitted data. A MAC is generated by combining the data with a secret key. The MAC ensures that the data has not been modified in transit and that it originated from a trusted source.
More about Replay attacks
In addition to the information provided in the previous sections, there are a few more things to know about replay attacks.
Firstly, it’s important to note that replay attacks can be both passive and active. A passive replay attack involves simply intercepting and replaying data packets, while an active replay attack involves modifying the data packets before replaying them. Active replay attacks can be even more dangerous than passive attacks because they can allow an attacker to modify the data being transmitted, potentially causing even more damage.
Another key factor to consider is the role that authentication protocols play in preventing replay attacks. Authentication protocols are used to ensure that data is being transmitted between trusted parties. However, if an attacker is able to intercept and replay authentication requests, they may be able to gain unauthorized access to a system or account. Therefore, it’s crucial to use strong authentication protocols that are resistant to replay attacks.
It’s important to understand that replay attacks are not the only threat to data security. There are many other types of cyberattacks, including phishing attacks, malware attacks, and denial-of-service attacks, among others. It’s important to have a comprehensive security strategy in place that addresses all potential threats to data security.
Also, replay attacks are a significant threat to data security that can result in financial losses, data loss or corruption, and unauthorized access to systems or accounts. Preventing replay attacks involves implementing various security measures, including timestamping, nonce values, encryption, and MACs. By understanding the threat of replay attacks and taking steps to prevent them, individuals and organizations can ensure the integrity and confidentiality of their data.
What to Do if You Are a Victim of a Replay Attack?
Here’s some additional information on what to do if you are a victim of a replay attack:
If you suspect that you are a victim of a replay attack, the first thing you should do is contact the relevant authorities, such as your bank or the IT department of your organization. They can help you determine the extent of the attack and take appropriate action to limit the damage.
In addition, you should change all of your passwords and other authentication credentials as soon as possible. This will prevent the attacker from using the same method to gain access to your accounts or systems in the future.
You should also ensure that all of your software and security systems are up to date, as replay attacks can often take advantage of vulnerabilities in outdated software.
If you have suffered financial losses as a result of a replay attack, you should contact your bank or credit card company immediately to report the issue and request a refund. Many banks and credit card companies have fraud protection programs in place that can help you recover your losses.
It’s crucial to learn from the experience and take steps to prevent future attacks. This may involve implementing additional security measures, such as two-factor authentication or more robust encryption protocols, or training employees on how to identify and prevent replay attacks.
All in all, if you are a victim of a replay attack, it’s important to take immediate action to limit the damage and prevent future attacks. This may involve contacting the authorities, changing your passwords, updating your software and security systems, and seeking refunds for any financial losses. By taking these steps and learning from the experience, you can protect yourself and your organization from the threat of replay attacks in the future.
In Conclusion
Replay attacks are a serious threat to data security. By intercepting and retransmitting data packets, an attacker can gain unauthorized access to systems, steal sensitive information, and cause significant financial losses. Preventing replay attacks involves implementing various security measures, such as timestamping, nonce values, encryption, and MACs.
As technology continues to advance, the need for robust security measures to protect sensitive information has become more critical. By understanding the threat of replay attacks and taking steps to prevent them, individuals and organizations can ensure the integrity and confidentiality of their data.